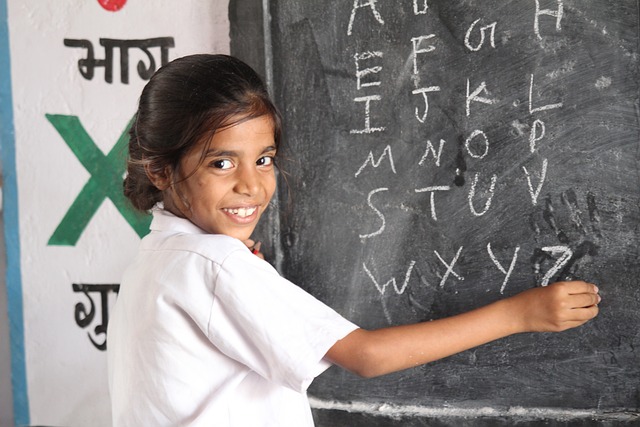電腦密碼

2023復習正是強化復習階段,在考研英語中占了40分,所以考研英語閱讀是英語科目中重要的一項。名師老師曾建議過考研生需要堅持每天泛讀10-15分鐘的英文原刊。強烈推薦了雜志《經濟學人》.雜志中的文章也是考研英語的主要材料來源.希望考研考生認真閱讀,快速提高考研英語閱讀水平。 Computer passwords 電腦密碼 Speak, friend, and enter 說,朋友和進入 Computer passwords need to be memorable andsecure. 電腦密碼須具備兩個特性:易記及難猜。 Most people s are the first but not the second. 但是大部分人的密碼只注重了前者卻忽略了后者。 Researchers are trying to make it easier for them to be both 研究人員正努力讓兩者兼而有之變得更以實現。 PASSWORDS are ubiquitous in computer security. 密碼在電腦安全領域的應用相當普遍。 All too often, they are also ineffective. 但他們往往沒起什么作用。 A good password has to be both easy to remember and hard to guess, but in practice peopleseem to plump for the former over the latter. 一個好密碼必須具備易記及難猜兩個特征,而實際上人們好像只注意到了前者而忽略了后者。 Names of wives, husbands and children are popular. 以妻子,丈夫或孩子的名字作為密碼的人大有人在。 Some take simplicity to extremes: one former deputy editor of The Economist used z formany years. 有些人的密碼簡單到了極點:The Economist的一位前副主編多年來一直用Z作密碼。 And when hackers stole 32m passwords from a social-gaming website called RockYou, itemerged that 1.1% of the site s users365,000 peoplehad opted either for 123456 or for12345. 當黑客在社交游戲網站盜取了3200萬用戶的密碼后,人們才發現原來這個網站大約1.1%的用戶-也就是365,000人-選擇了12345或123456作為密碼。 That predictability lets security researchers create dictionaries which list commonpasswords, a boon to those seeking to break in. 安全性研究人員于是根據密碼的這種可預見性編制了一些羅列處各種常見密碼的字典,這對那些有志于破解他人密碼的人來說可說是找到了福音。 But although researchers know that passwords are insecure, working out just how insecurehas been difficult. 但即使研究人員已經知道了密碼不安全,要確切地給出個不安全系數卻是很困難的。 Many studies have only small samples to work ona few thousand passwords at most. 許多研究項目的對象只有一小塊樣本-最多只有幾千個密碼。 Hacked websites such as RockYou have provided longer lists, but there are ethical problemswith using hacked information, and its availability is unpredictable. 像Rockyou這樣被黑的網站能夠提供更多的密碼,但使用黑客盜取的密碼不僅會引發道德問題上的爭議,其可行性也是未知的。 However, a paper to be presented at a security conference held under the auspices of theInstitute of Electrical and Electronics Engineers, a New York-based professional body, inMay, sheds some light. 然而,在五月份由總部位于紐約的一個專業組織-電氣電子協會支持下召開了一場安全性研討會議,會上公布的一份文件讓我們看到了解決這個難題的一絲曙光。 With the co-operation of Yahoo!, a large internet company, Joseph Bonneau of CambridgeUniversity obtained the biggest sample to date70m passwords that, though anonymised,came with useful demographic data about their owners. 在一家大型網絡公司-雅虎的協助下,劍橋大學的Joseph Bonneau得到了一份迄今為止最大的研究樣本,雖然是匿名的,但是包含了其用戶極為有用的人口學數據。 Mr Bonneau found some intriguing variations. 在這份樣本中Mr Bonneau發現了一些有趣的差異。 Older users had better passwords than young ones. 相較于年輕用戶,老用戶設置的用戶更好。 People whose preferred language was Korean or German chose the most secure passwords;those who spoke Indonesian the least. 母語為韓語或德語的用戶所設置的密碼安全系數最高,而說印尼語的最低。 Passwords designed to hide sensitive information such as credit-card numbers were onlyslightly more secure than those protecting less important things, like access to games. 被設置用來隱藏像信用卡卡號這樣的敏感信息的密碼,相比較于另外一些保護游戲登錄入口這樣不那么重要的信息所設置的密碼,其安全性高不了多少。 Nag screens that told users they had chosen a weak password made virtually no difference. 那些提醒用戶設置的密碼安全性較低的嘮叨屏幕其實沒有什么作用。 And users whose accounts had been hacked in the past did not make dramatically moresecure choices than those who had never been hacked. 相對于那些從沒被黑過的,有過賬戶被黑經驗的用戶的安全防范意識也并沒得到顯著提高。 But it is the broader analysis of the sample that is of most interest to security researchers. 但是,對研究樣本進行更為綜合性的分析才是安全性研究人員的興趣所在。 For, despite their differences, the 70m users were still predictable enough that a genericpassword dictionary was effective against both the entire sample and any demographicallyorganised slice of it. 因為盡管存在各種差異,但是通過分析樣本中那7000萬用戶的資料還是可以預見到,一部通用的密碼暴力破解字典就能夠有效應付這一整個樣本,或者任何根據某項人口學特征而從中抽取的一小塊資料。 Mr Bonneau is blunt: An attacker who can manage ten guesses per accountwillcompromise around 1% of accounts. Mr Bonneau直言不諱地說:只要每個賬號給破解者10次猜測密碼的機會...會有大約1%的密碼被破解。 And that, from the hacker s point of view, is a worthwhile outcome. 這在黑客看來絕對值得一試。 One obvious answer would be for sites to limit the number of guesses that can be madebefore access is blocked, as cash machines do. 對網站而言,很顯然,他們可以在系統上進行類似于ATM機的設置:一旦密碼輸入錯誤次數達到規定者,即封鎖登錄入口。 Yet whereas the biggest sites, such as Google and Microsoft, do take such measures,many donot. 然而,只有谷歌、微軟這樣的大型網站采取了類似的措施,很多其他網站對此不以為意。 A sample of 150 big websites examined in 2010 by Mr Bonneau and his colleague SrenPreibusch found that 126 made no attempt to limit guessing. 在2010年,Mr Bonneau和他的同事Sren Preibusch曾對一份囊括了150家大型網站的樣本做過調查,結果顯示其中126家并沒有對密碼輸入錯誤次數作出限制。 How this state of affairs arose is obscure. 這種狀況的狀況的出現實在是令人費解。
2023復習正是強化復習階段,在考研英語中占了40分,所以考研英語閱讀是英語科目中重要的一項。名師老師曾建議過考研生需要堅持每天泛讀10-15分鐘的英文原刊。強烈推薦了雜志《經濟學人》.雜志中的文章也是考研英語的主要材料來源.希望考研考生認真閱讀,快速提高考研英語閱讀水平。 Computer passwords 電腦密碼 Speak, friend, and enter 說,朋友和進入 Computer passwords need to be memorable andsecure. 電腦密碼須具備兩個特性:易記及難猜。 Most people s are the first but not the second. 但是大部分人的密碼只注重了前者卻忽略了后者。 Researchers are trying to make it easier for them to be both 研究人員正努力讓兩者兼而有之變得更以實現。 PASSWORDS are ubiquitous in computer security. 密碼在電腦安全領域的應用相當普遍。 All too often, they are also ineffective. 但他們往往沒起什么作用。 A good password has to be both easy to remember and hard to guess, but in practice peopleseem to plump for the former over the latter. 一個好密碼必須具備易記及難猜兩個特征,而實際上人們好像只注意到了前者而忽略了后者。 Names of wives, husbands and children are popular. 以妻子,丈夫或孩子的名字作為密碼的人大有人在。 Some take simplicity to extremes: one former deputy editor of The Economist used z formany years. 有些人的密碼簡單到了極點:The Economist的一位前副主編多年來一直用Z作密碼。 And when hackers stole 32m passwords from a social-gaming website called RockYou, itemerged that 1.1% of the site s users365,000 peoplehad opted either for 123456 or for12345. 當黑客在社交游戲網站盜取了3200萬用戶的密碼后,人們才發現原來這個網站大約1.1%的用戶-也就是365,000人-選擇了12345或123456作為密碼。 That predictability lets security researchers create dictionaries which list commonpasswords, a boon to those seeking to break in. 安全性研究人員于是根據密碼的這種可預見性編制了一些羅列處各種常見密碼的字典,這對那些有志于破解他人密碼的人來說可說是找到了福音。 But although researchers know that passwords are insecure, working out just how insecurehas been difficult. 但即使研究人員已經知道了密碼不安全,要確切地給出個不安全系數卻是很困難的。 Many studies have only small samples to work ona few thousand passwords at most. 許多研究項目的對象只有一小塊樣本-最多只有幾千個密碼。 Hacked websites such as RockYou have provided longer lists, but there are ethical problemswith using hacked information, and its availability is unpredictable. 像Rockyou這樣被黑的網站能夠提供更多的密碼,但使用黑客盜取的密碼不僅會引發道德問題上的爭議,其可行性也是未知的。 However, a paper to be presented at a security conference held under the auspices of theInstitute of Electrical and Electronics Engineers, a New York-based professional body, inMay, sheds some light. 然而,在五月份由總部位于紐約的一個專業組織-電氣電子協會支持下召開了一場安全性研討會議,會上公布的一份文件讓我們看到了解決這個難題的一絲曙光。 With the co-operation of Yahoo!, a large internet company, Joseph Bonneau of CambridgeUniversity obtained the biggest sample to date70m passwords that, though anonymised,came with useful demographic data about their owners. 在一家大型網絡公司-雅虎的協助下,劍橋大學的Joseph Bonneau得到了一份迄今為止最大的研究樣本,雖然是匿名的,但是包含了其用戶極為有用的人口學數據。 Mr Bonneau found some intriguing variations. 在這份樣本中Mr Bonneau發現了一些有趣的差異。 Older users had better passwords than young ones. 相較于年輕用戶,老用戶設置的用戶更好。 People whose preferred language was Korean or German chose the most secure passwords;those who spoke Indonesian the least. 母語為韓語或德語的用戶所設置的密碼安全系數最高,而說印尼語的最低。 Passwords designed to hide sensitive information such as credit-card numbers were onlyslightly more secure than those protecting less important things, like access to games. 被設置用來隱藏像信用卡卡號這樣的敏感信息的密碼,相比較于另外一些保護游戲登錄入口這樣不那么重要的信息所設置的密碼,其安全性高不了多少。 Nag screens that told users they had chosen a weak password made virtually no difference. 那些提醒用戶設置的密碼安全性較低的嘮叨屏幕其實沒有什么作用。 And users whose accounts had been hacked in the past did not make dramatically moresecure choices than those who had never been hacked. 相對于那些從沒被黑過的,有過賬戶被黑經驗的用戶的安全防范意識也并沒得到顯著提高。 But it is the broader analysis of the sample that is of most interest to security researchers. 但是,對研究樣本進行更為綜合性的分析才是安全性研究人員的興趣所在。 For, despite their differences, the 70m users were still predictable enough that a genericpassword dictionary was effective against both the entire sample and any demographicallyorganised slice of it. 因為盡管存在各種差異,但是通過分析樣本中那7000萬用戶的資料還是可以預見到,一部通用的密碼暴力破解字典就能夠有效應付這一整個樣本,或者任何根據某項人口學特征而從中抽取的一小塊資料。 Mr Bonneau is blunt: An attacker who can manage ten guesses per accountwillcompromise around 1% of accounts. Mr Bonneau直言不諱地說:只要每個賬號給破解者10次猜測密碼的機會...會有大約1%的密碼被破解。 And that, from the hacker s point of view, is a worthwhile outcome. 這在黑客看來絕對值得一試。 One obvious answer would be for sites to limit the number of guesses that can be madebefore access is blocked, as cash machines do. 對網站而言,很顯然,他們可以在系統上進行類似于ATM機的設置:一旦密碼輸入錯誤次數達到規定者,即封鎖登錄入口。 Yet whereas the biggest sites, such as Google and Microsoft, do take such measures,many donot. 然而,只有谷歌、微軟這樣的大型網站采取了類似的措施,很多其他網站對此不以為意。 A sample of 150 big websites examined in 2010 by Mr Bonneau and his colleague SrenPreibusch found that 126 made no attempt to limit guessing. 在2010年,Mr Bonneau和他的同事Sren Preibusch曾對一份囊括了150家大型網站的樣本做過調查,結果顯示其中126家并沒有對密碼輸入錯誤次數作出限制。 How this state of affairs arose is obscure. 這種狀況的狀況的出現實在是令人費解。